Microsoft officials shared some more information about new secure boot experience in Windows 8 powered by UEFI.
In this blog post, I’m going to share a different approach about Windows 8 and UEFI, from Inside Out.
Let’s start with UEFI.
In simple terms, the UEFI stands for Unified Extensible Firmware Interface, a protocol that defines a software interface between an operating system and platform firmware. UEFI is a replacement for the older BIOS firmware interface.
UEFI secure boot (for more details, read Chapter 27 of the UEFI 2.3.1 specification) helps reduce the risk of boot loader attacks by validating firmware images before they are allowed to execute and it is not Windows 8 feature.
Windows 8 just utilizes secure boot to ensure pre-OS environment protection. UEFI is mandatory and Windows 8 will continue to support the legacy BIOS interface, but machines using the UEFI interface will have significantly better security capabilities.
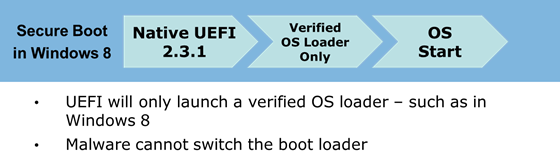
How UEFI secure boot takes place in Windows 8 boot experience.
Non-UEFI systems are vulnerable to attacks by redirecting the boot loader handoff to possible malicious loaders. And in absence of security measures in pre-OS environment, these loaders remain undetected to operating system security solutions.

Windows 8 addresses this vulnerability with UEFI secure boot, and using policy present in firmware along with certificates to ensure that only properly signed and authenticated components are allowed to execute.
It is good for Windows platform all the way!
No more BIOS emulated activation cracks – Since UEFI authenticates components and blocks malicious loaders, therefore fake BIOS emulation can’t be possible and cracks like Windows 7 Loader no longer works.
(It may help to prevent piracy, but where there’s will there’s way)
No more bootkit and rootkit attacks – It immunes from bootkit and rootkit attacks that target system vulnerabilities before the operating system itself even loads.
I read some blog posts “Windows 8 secure boot experience blocks non-Windows loaders.” It’s just a myth. Secure boot is a policy that allows firmware to validate authenticity of components and doesn’t lock out any operating system loaders.
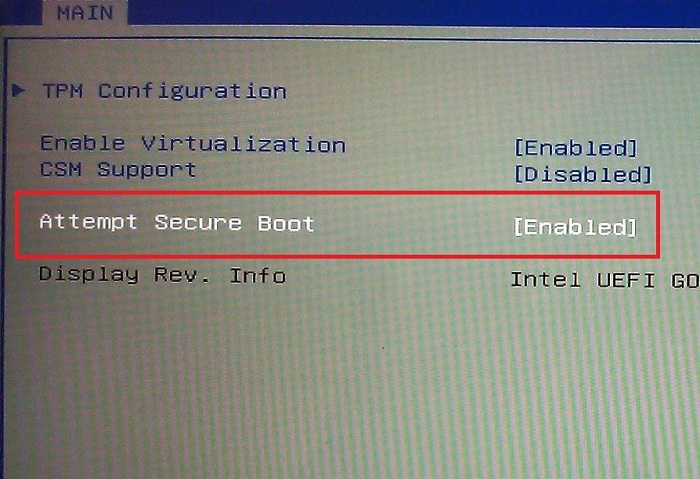
Note: OEMs have the ability to customize their firmware to meet the needs of their customers by customizing the level of certificate and policy management on their platform.
Since Windows has become more stable and secure; now the balls are in non-Windows’ court and we are to see how they are going to deal with it.

Leave a Reply